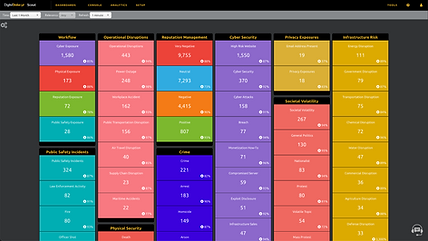
Cyber Risk Taxonomy for Cyber Intelligence
Cyber Security Taxonomy for safeguarding digital assets and data. Understand critical cyber threats, strategic response measures, and best practices in the ever-evolving digital security landscape.
Overview of Cyber Intelligence
Cyber Intelligence involves the collection, analysis, and dissemination of information about threats and vulnerabilities in the digital realm. This discipline is crucial for protecting organizations from cyber risks such as data breaches, malware attacks, and cyber espionage.
Components of Cyber Intelligence
Threat Intelligence
Threat intelligence focuses on identifying and analyzing potential cyber threats, including threat actors, their motivations, and their tactics, techniques, and procedures (TTPs).
Vulnerability Intelligence
Vulnerability intelligence involves the identification and assessment of weaknesses in systems, networks, and applications that could be exploited by threat actors.
Strategic Intelligence
Strategic intelligence provides a broader view of the cyber threat landscape, including emerging trends, geopolitical factors, and long-term cybersecurity implications for organizations.
Importance of Cyber Intelligence
Cyber Intelligence is vital because it:
1. Protects Digital Assets
Cyber intelligence helps safeguard an organization's critical digital assets, including:
Sensitive customer data
Intellectual property
Financial information
Operational systems and infrastructure
2. Enables Proactive Risk Mitigation
By providing early warning of potential threats, cyber intelligence allows organizations to:
Implement preventive measures
Patch vulnerabilities before they can be exploited
Adjust security strategies based on emerging threats
3. Enhances Cybersecurity Posture
Cyber intelligence contributes to a robust cybersecurity posture by:
Informing security investments
Guiding the development of incident response plans
Supporting continuous improvement of security practices
4. Supports Regulatory Compliance
Cyber intelligence helps organizations:
Meet data protection requirements
Demonstrate due diligence in cybersecurity practices
Prepare for and respond to audits effectively
5. Ensures Business Continuity
By helping prevent and mitigate cyber incidents, cyber intelligence supports:
Uninterrupted business operations
Protection of brand reputation
Maintenance of customer trust
Sample Cyber Event Types/Descriptions
1. Data Breach
Incidents involving unauthorized access to sensitive or confidential data, potentially leading to:
Data theft
Exposure of personal information
Compliance violations
2. Malware Distribution
The spread of malicious software designed to:
Disrupt normal computer operations
Gain unauthorized access to systems
Steal sensitive information
3. Phishing
Deceptive attempts to obtain sensitive information by:
Impersonating trustworthy entities
Using social engineering tactics
Exploiting human vulnerabilities
4. DDoS Attack
Distributed Denial of Service attacks that:
Overwhelm target systems or networks
Render services unavailable to legitimate users
Potentially mask other malicious activities
5. Ransomware
Malicious software that:
Encrypts valuable data
Demands ransom for data release
Potentially causes significant operational disruptions
Sample Cyber Article Titles
"Breaking: Major Tech Company Suffers Massive Data Breach, Millions of User Accounts Compromised"
"Global Ransomware Attack Cripples Healthcare Systems Across Multiple Countries"
"New Sophisticated Phishing Campaign Targets C-Suite Executives Worldwide"
"Critical Zero-Day Vulnerability Discovered in Widely-Used Enterprise Software"
"State-Sponsored Hackers Launch Coordinated Cyber Espionage Campaign Against Defense Contractors"
Sample Courses of Cyber Action/Recommendations
1. Immediate Incident Response
Isolate affected systems to prevent further spread
Activate the cybersecurity incident response team
Initiate predefined incident response protocols
2. Rapid Security Assessment
Identify the extent of the breach or attack
Determine potential data exfiltration or damage
Assess the impact on critical business operations
3. Vulnerability Mitigation
Implement emergency patches and updates
Address critical vulnerabilities across all systems
Conduct penetration testing to verify mitigation effectiveness
4. Enhanced Monitoring and Detection
Increase logging and monitoring capabilities
Deploy additional intrusion detection/prevention systems
Implement advanced threat hunting techniques
5. Stakeholder Communication
Initiate crisis communication plans
Inform employees, customers, and partners as appropriate
Comply with regulatory reporting requirements